Access Control System
AWARE is a trusted provider of advanced access control systems designed to enhance the performance and security of your offices and buildings. In today's modern business landscape, access control systems are an essential requirement. Our highly adaptable system streamlines door-to-door entries, ensuring only authorized personnel gain entry.
With our access control system in place, you can create a safe environment, mitigate the risk of theft, maintain a comprehensive record of individuals entering and exiting your premises, and effectively ward off unwanted visitors.
AWARE's Access Control System (ACS) offers extensive support for multiple devices, cards, card readers, and more. Our state-of-the-art system operates through both physical and virtual means of authentication. Physical authentication allows for secure access using ID cards or biometric credentials, while virtual authentication leverages data and computer networks for enhanced security.
Ensuring Reliable Access Authorization
Maintaining a high-security system necessitates thorough credential verification. Only through a robust credential assessment can a system be fortified, effectively protecting data and networks. AWARE's access control system ensures the accuracy of credential records, addressing concerns regarding credential vulnerability frequently encountered in large businesses. Our ACS is specifically designed with this crucial aspect in mind, prioritizing the security of credentials to uphold a robust security infrastructure.
Enhanced User Experience
At AWARE, we understand that customers consistently hold high expectations when it comes to user experience. That's why our access control system is meticulously designed with the user in mind, as we firmly believe that a seamless user experience is integral to a superior security system.
We are dedicated to ensuring the utmost satisfaction of our users by prioritizing an intuitive interface and eliminating any potential errors. By streamlining the system's usability and guaranteeing a hassle-free experience, we strive to provide an enhanced user experience that surpasses expectations.
Monitor Guest Activity
Ensure the utmost security of your premises by effectively monitoring and managing visitor access. With AWARE's advanced access control system, you can grant appropriate access permissions to visitors while they conveniently sign in, creating a secure and protected environment. Our cutting-edge technology seamlessly integrates with your existing infrastructure, providing comprehensive safety and peace of mind.
Advanced Security Solutions: Fortifying Protection
Maintaining the highest level of security of user credentials is of paramount importance. A comprehensive security system is essential to safeguard users' data and maintain their privacy effectively. AWARE's access control system seamlessly integrates with an enhanced security framework, providing the highest level of protection for our valued customers. By strictly limiting access to authorized users only, we guarantee that information remains accessible solely to those with proper authorization.

Access Control Systems for your Business Needs

Corporate Offices
High-security office spaces are the backbone of every thriving business.

Educational institutions
Top-tier security for educational institutions' premises.

Financial Sector
Ensuring the safety of individuals and assets while efficiently managing restricted areas.

Healthcare
Secure environment within hospitals, promoting the safety of visitors, patients, and staff members alike.
Power structures
Establishing authorized entry points to the power station while ensuring comprehensive security of the premises.
Public Places
Ensuring the safety and security of public entry points, such as shopping centers and exhibition sites.
Readers
The access control system incorporates various types of readers, including barcode readers, magnetic stripe readers, smart card readers, proximity readers, and more. These devices play a crucial role in reading credentials and granting access to specific points within the premises. By facilitating convenient entry while effectively limiting unauthorized access, these reader devices significantly contribute to maintaining a highly secure environment. Whether for small businesses or large enterprises, readers are consistently recognized as valuable assets in ensuring safety and security.


Biometric readers
Biometric readers analyze unique behavioral and physical traits of individuals, comparing them with a database to verify their identity. Biometric readings encompass advanced technologies such as iris scanning, facial recognition, fingerprint recognition, and palm vein recognition. These biometric data points are utilized to grant or deny access to specific areas. Leveraging the statistical analysis of behavioral and physical characteristics, biometric readers provide top-level security, ensuring robust protection for sensitive locations.

Intrusion Alarms
Intrusion alarms are utilized to detect and deter unauthorized or unwanted access to specific areas, serving both commercial and residential purposes. The primary objective of intrusion alarms is to effectively monitor and control physical access to designated areas, assets, and systems. These alarms employ a specialized mechanism that detects door or window movement and triggers a loud alarm signal, alerting individuals to the potential breach and enhancing security measures.

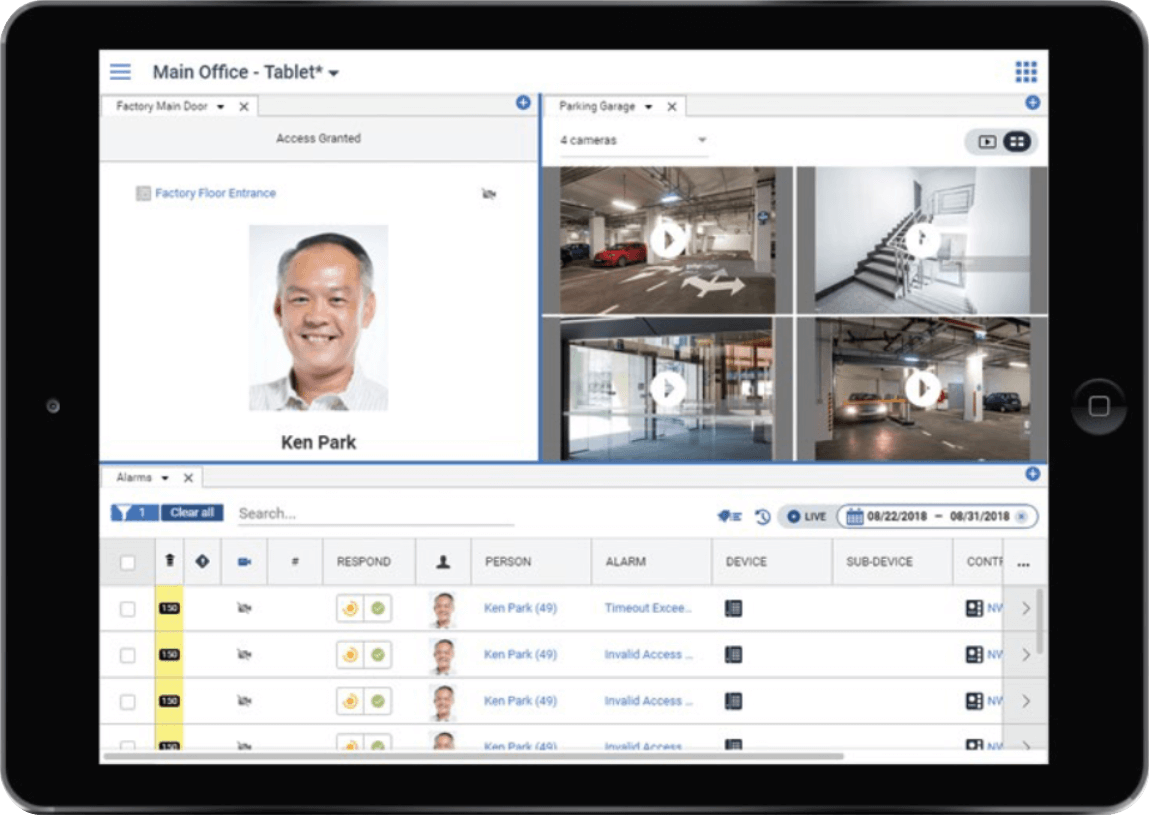
Integrations of Alarms, Video, and Devices
One of the most notable advantages of an access control security system lies in its seamless integration of alarms and video surveillance. This integration not only enhances operational efficiency and user-friendliness but also significantly elevates overall security measures. By integrating alarms and video within the access control system, companies gain valuable insights into authorized personnel accessing their premises and receive immediate alerts in the event of unauthorized entry. This allows swift action to be taken when necessary. The consolidation of these components into a single platform greatly improves the user experience, eliminating the need to navigate multiple systems independently. Furthermore, the integration with devices enables users to easily manage and monitor potential intrusions from any location, providing a device-centric approach that ensures comprehensive security awareness.
Our
International Partners